You can also watch this video on LBRY
- New report by ESET highlights every known attempted airgap hack utilised a USB drive
What is Air Gapping?
The most important and sensitive computer systems on the planet are airgapped. Airgapping means isolating a computer system or network from all other networks, and most importantly this means no internet access at all.
No external network access is inconvenient, but as far as protecting a computer system goes, air gapping is the ultimate defense. Malware almost always originates from some outside threat, whether that’s a dodgy link, or an evil email - so the best catch-all solution to prevent these threats is simply to disconnect from WiFi and cut your ethernet cables.
This approach, is often used for industrial systems, power grids, anything that has “nuclear” in the name, and pipelines. Fun fact, when it comes to the recent colonial pipeline hack that caused fuel shortages and havoc in parts of America, the pipeline itself wasn’t hacked at all, in fact it was fine - the airgapping did its job, what was hacked was the billing system which monitors the flow of fuel. What’s the point of pumping fuel if you can’t charge for it? And so they shut the whole thing down.
Air Gapping may be a good defense, but people (specifically governments) are going to want to hack juicy targets no matter what obstacles are in their way. Cybersecurity company ESET has analysed every single known case of hackers trying to break into airgapped systems, which has only happened 17 times globally - that we know of at least. ESET came to a peculiar discovery. Every single hack had one common trait. “They all used weaponized USB drives” - this is such an important point.
How To Hack An Air Gapped System
So how do you hack an airgapped system with a USB drive? Typically a facility, for example a nuclear power station isn’t going to be 100% airgapped. Even a facility like this still needs people to man the phone lines, answer emails, and so on. So these people will work on an internet connected network, but the idea is that even if this network is hacked, no amount of lateral movement or privilege escalation will get a hacker what they want - because the control systems that handle all the fun and juicy stuff will be airgapped from this network and the wider internet.
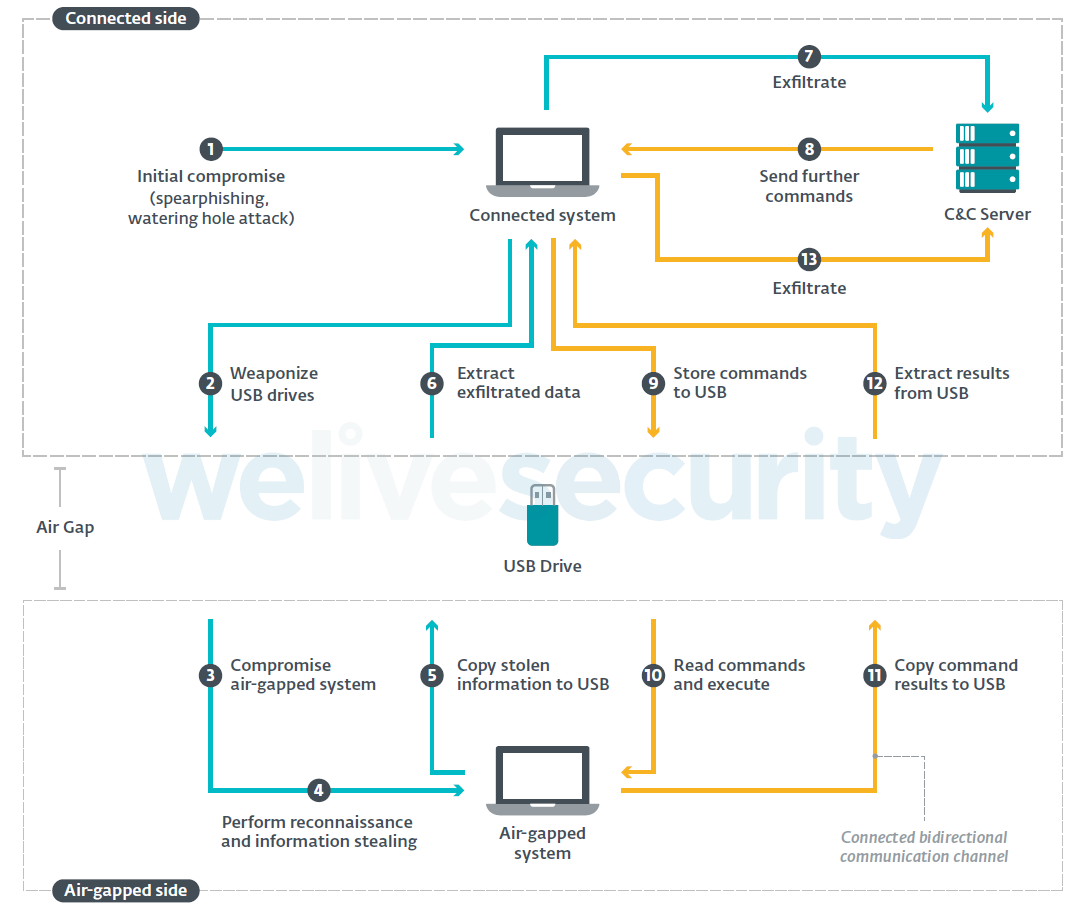
Usually the plan of attack is to first somehow compromise the system which is connected to the internet, then install malware on this system which automatically weaponizes connected USB sticks. Then hope that one of these USB sticks somehow makes its way to the airgapped system. How? Well employees might need to update software on the airgapped system they’re going to use a USB drive, or maybe an employee uses a USB stick to store a portable version of minecraft for when they get bored, who knows? After the malicious USB stick installs malware on the air gapped system, it performs reconnaissance, then stolen data is copied back to the USB stick until it is plugged back into the already compromised connected system where it is then exfiltrated to the attacker controlled command and control server.
Sometimes the attackers program in the ability to send further commands to the malware, so they can change the plan of attack as they go.
irl Examples
One airgap hack was given the name 'PlugX' - the purpose of this hack was to “Perform espionage against unknown entities” unfortunately, as with many hacks, the whole story isn’t public so we don’t know who the victim was here or even what kind of facility was being attacked. The initial compromise targeted a connected part of the unknown entity’s network through malware laden spearphishing emails. Once the plugX malware had been installed, it “monitored for the arrival of USB drives and weaponized them”. Their method of weaponization wasn’t rocket science at all, but it is sneaky. On the USB drive the malware created a hidden folder called recycle.bin, and put their malware inside of it. Then it made shortcut files which pointed to the malware in the hidden folder, open the shortcut and you open the malware. The shortcuts were given a folder icon - disguising them.
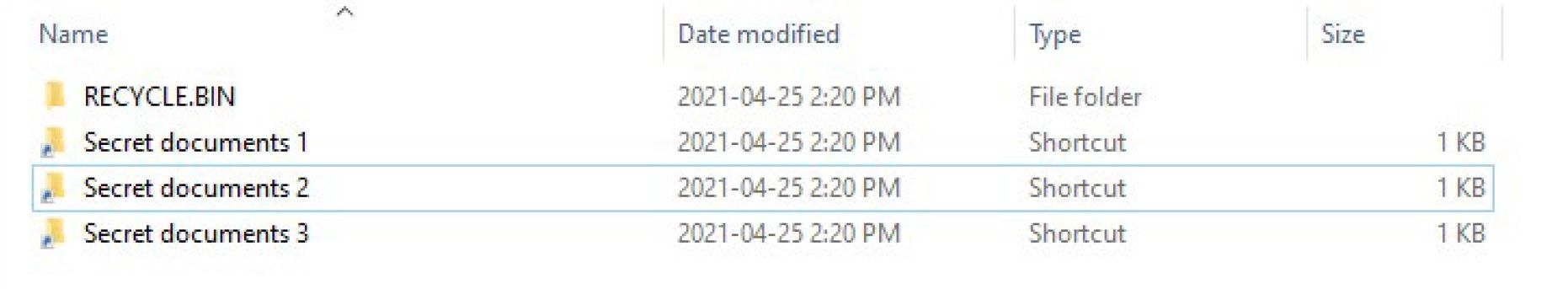
The hope was, an unwitting victim would then plug this USB drive into the airgapped network, then their curiosity would get the better of them, they’d wonder what these strange folders are, then they’d open one of the shortcuts, triggering the malware. The malware would scan the system for certain documents, encrypt them and copy them back to the USB drive, until it was plugged back into the connected system from which they would then be exfiltrated over the interwebs to the hackers.
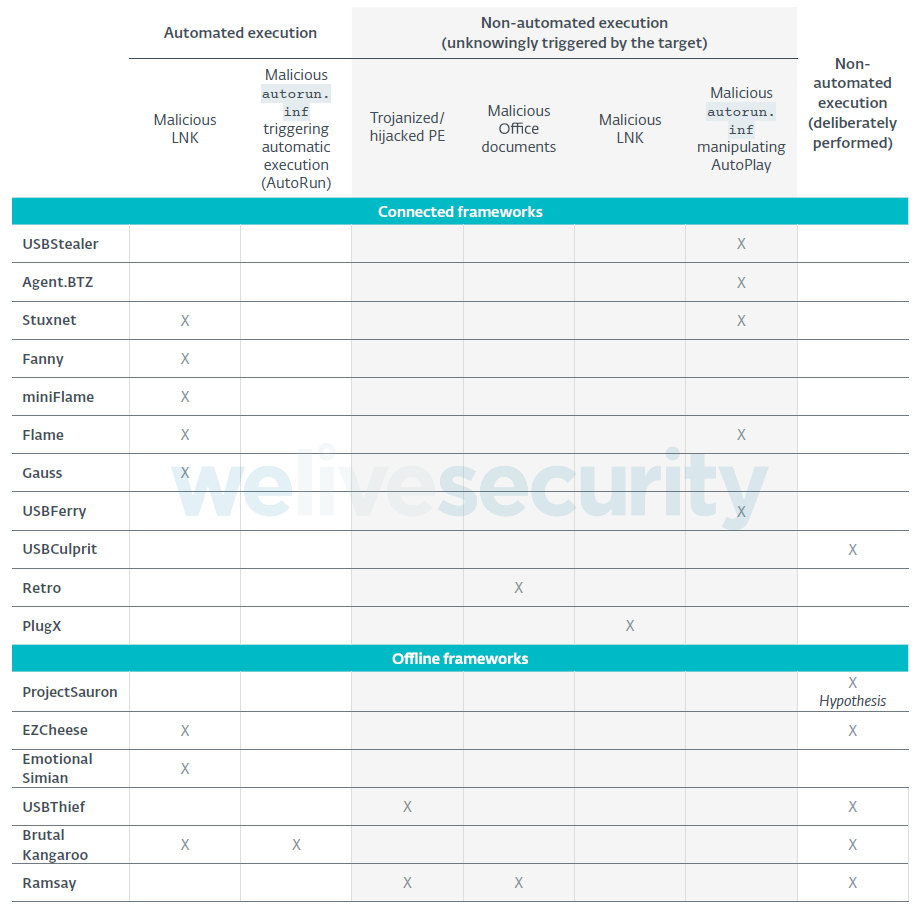
The PlugX hack is an example of non-automated execution, in that the malware on the USB stick has to be manually run by an unwitting victim. Though some USB hacks fall into the automated category, these hacks don’t require any user interaction at all, just plugging in a USB drive is enough to pwn the air gapped system - these are infinitely more advanced than just hoping someone double clicks on a disguised shortcut.
The most notorious example of this comes in the form of stuxnet. Stuxnet was a joint US and Israeli mission to hack into Iran’s Natanz nuclear facility, which resulted in the destruction of 10% of Iranian centrifuges used to enrich uranium. That hack utilised a now famous vulnerability which exploited a remote code execution bug in windows shortcut icons. As soon as the icon loaded on the target PC, malicious code was executed. This required no human interaction at all, other than opening the folder the exploited file was located in.
Hacking an airgapped system isn’t straightforward, all 17 known hacks were carried out by APTs - advanced persistent threats. None of these hacks were money making activities, all 17 of our cases “shared a common purpose: espionage.”
Crazy Data Exfiltration Methods
Other than USB sticks, there are some more interesting and creative ways to exfiltrate data. One commonly cited example is using the speakers of an air gapped computer to transmit data encoded in ultrasonic sound waves; humans can’t hear these, but an attacker could record this sound and decode the data. One slightly more crazy example is called “Fansmitter”, it takes a use case where an infected computer has no speakers, instead it encodes data in the sound emitted by a computer’s CPU and chassis fans - it does this simply by changing the fan speed. This isn’t totally theoretical, there’s a research paper on this and even a demonstration video. However these examples are completely academic, there’s been no known example of these methods being used in the wild.
ESET have also detailed some ways of “defending air gapped networks”, they haven’t discovered any groundbreaking new techniques though, they’ve mostly rehashed tried and true methods like “disabling USB ports on air gapped systems” and “keeping systems updated”.