You can also watch this video on LBRY
2021 has been a year of some very epic hacks. Here are my top 5 favourite which stood out to me personally, in no particular order.
Twitch Hack
Back in October the entirety of twitch was leaked by hackers on 4chan. The 128GB torrent included the entirety of Twitch’s codebase, including all their apps, internal SDKs, and it even revealed a secret project in development by Twitch, a steam competitor called vapor.
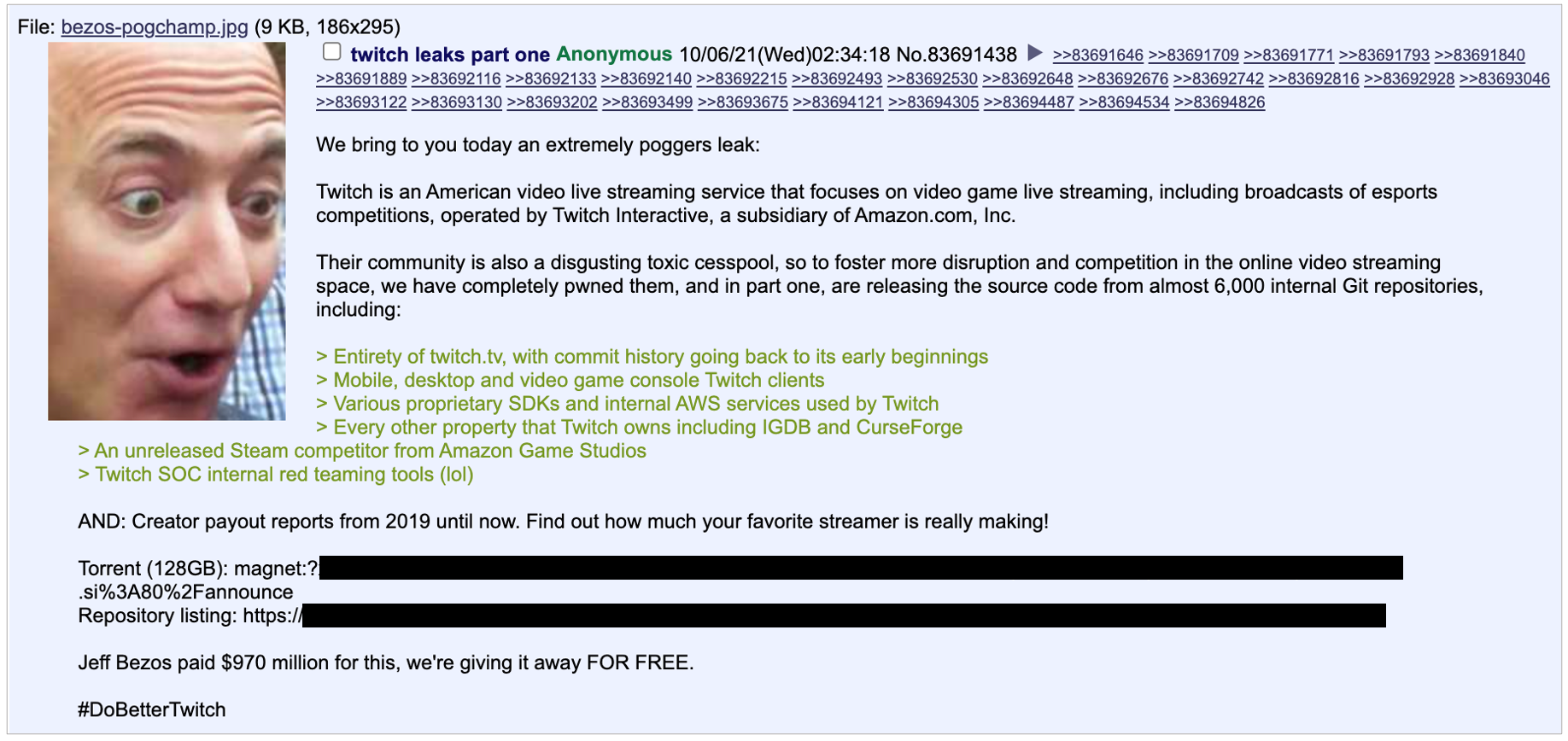
Top streamers’ earnings were also in the dump, which was the only thing the mainstream media latched on to when it came to this hack, though it did spawn some pretty solid memes.

This wasn’t a ransomware attack, or some kind of money making mission. Whoever was behind this seems to have had some beef with Twitch. Though the leaker does justify this hack by means other than pure spite, noting it was done “to foster more disruption and competition in the online video streaming space, we have completely pwned Twitch” - If this was the plan, I’m not sure it’s done its job, I’m yet to see any competitors using forked twitch code.
The hacker, who was never identified apparently got in through “an error in a Twitch server configuration change” - looks like a system that was meant to be air gapped was accidentally connected to the internet. Unsurprisingly Twitch downplayed the hack. Whilst the original 4chan post was titled “part 1”, the sequel, if there ever even was one, was never released.
Epik Dump
In September, the controversial hosting provider Epik was hacked. Epik made a name for themselves by hosting websites deplatformed by silicon valley, in doing so they’ve made quite a few enemies. On September 13th a group claiming to be Anonymous leaked 180GB of what can only be described as pure humiliation for Epik.
The leak includes such things as domain purchases, payment history, account credentials and so on, it’s a really long list. And to make matters worse, the dump revealed that Epik had been storing passwords as unsalted MD5 hashes, which is quite remarkable in 2021.
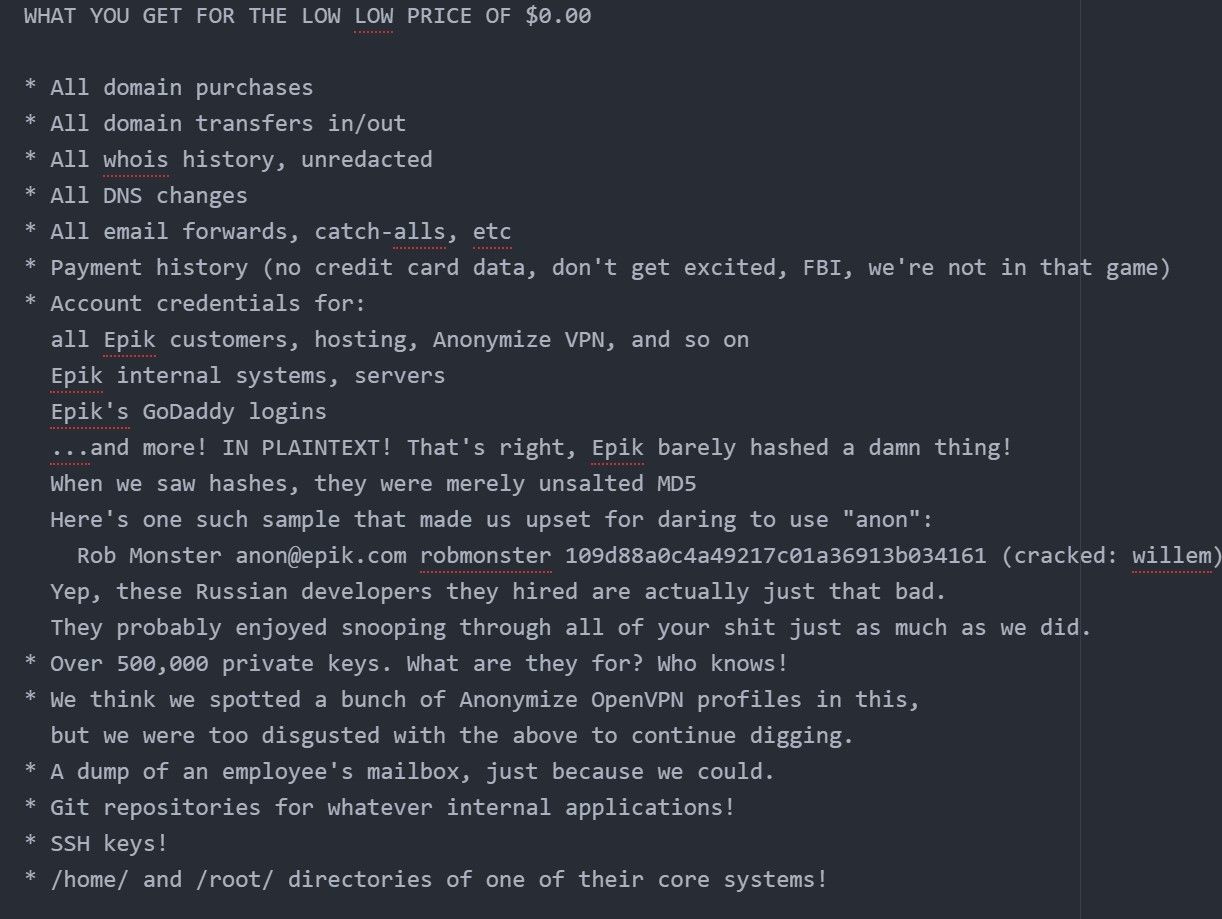
Anonymous aptly named the breach ‘Epik Fail’ - because how could you not? After the leak went live Epik initially refused to even acknowledge the hack, in response the miscreants published a blog post on Epik’s own website, making fun of them.
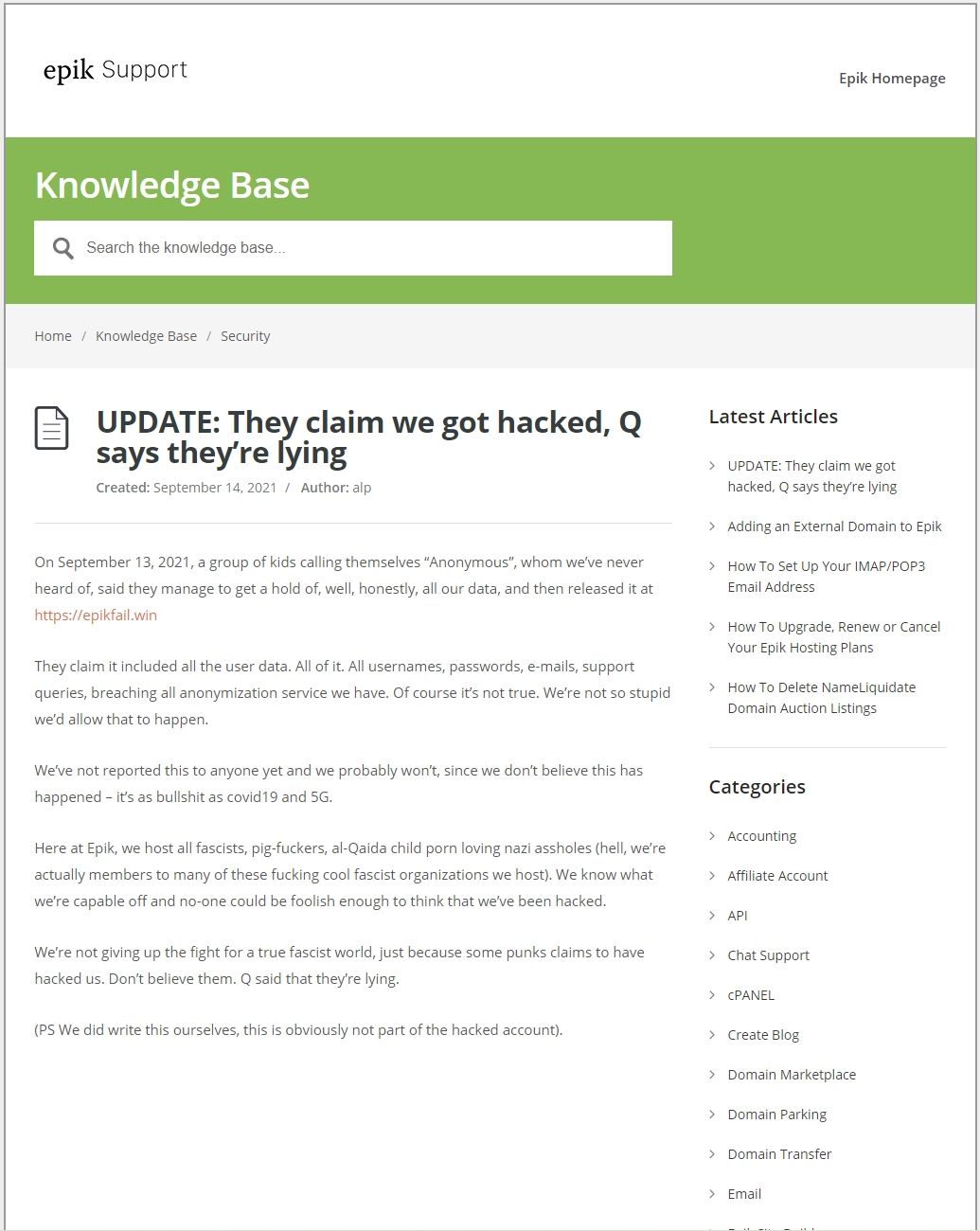
After finally acknowledging the breach, the CEO sent probably the strangest breach disclosure email I’ve ever seen, in which he said he was praying for his customers...
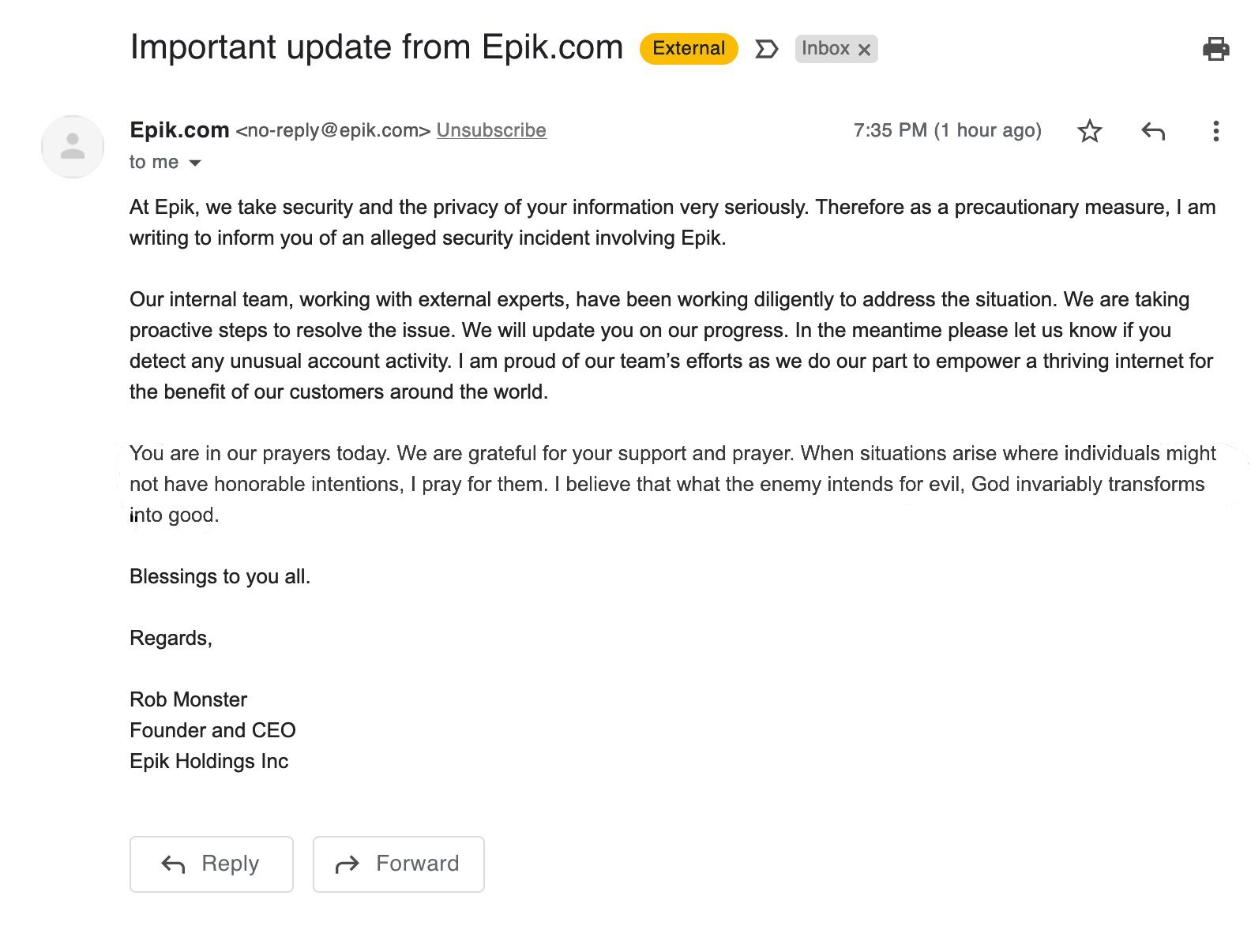
As for the cause of the breach, a remote code execution bug was discovered in Epik’s website in January of this year, the researcher who found it tried reporting it to the CEO but he was just ignored. The bug was a decade old, and allowed anyone to remotely run code on Epik’s servers without any authentication. This is the best guess as to how the hack went down.
Microsoft Exchange Vulnerabilities
This was arguably the most serious saga of hacks in the whole of 2021. It all started on January 5th when a security researcher who is well known for their work tweeted they had stumbled across “the most serious [remote code execution flaw they] have ever reported!”
Just report a pre-auth RCE chain to the vendor. This might be the most serious RCE I have ever reported! Hope there is no bug collision or duplicate😝
— Orange Tsai 🍊 (@orange_8361) January 5, 2021
It was discovered that there were a total of 4 rather scary vulnerabilities in Microsoft exchange. Specifically this affected on-premises exchange servers, these are email servers run by organisations themselves in their own offices and on their own physical hardware - but running Microsoft’s exchange software. The 4 vulnerabilities collectively gave attackers the ability to falsely authenticate as a standard user, escalate their privileges to that of an administrator and then inject malicious code into the server.
For organisations that use Microsoft Exchange, of which there are many, think businesses, NGOs, governments even, and so on. For these organisations this was essentially a doomsday kind of scenario, you had a situation where an attacker could remotely, with only knowledge of your ip address, gain admin rights to a server which held access to all of your emails.
Microsoft accused the cyber-espionage group “Hafnium” of targeting certain customers with these exploits, this group “Hafnium” is alleged to have ties to the Chinese government. However other cybercrime groups quickly caught wind of the exploits, and it wasn’t long until the situation devolved into a free for all, with mass scanning of ip’s underway by various groups, identifying vulnerable servers, before trying to somehow profit. Whether with ransomware, cryptomining, or some other flavour of illegal.
Microsoft eventually released patches, but not before 250,000 servers apparently fell victim to some level of exploitation.
FRAG Attacks
In May we heard about Frag Attacks. Frag Attacks was a whole suite of vulnerabilities discovered in WiFi. These hacks were quite remarkable in that some of them have been laying around undiscovered for over 24 years, since the very first version of WiFi itself, and so every single version of WiFi was vulnerable, even the brand new and barely even unwrapped WPA3.
One of the headline vulnerabilities discovered, enabled an attacker to inject packets into a network even if the network was password protected. In one example the researcher manages to turn on and off an IOT lightbulb connected to a network that he doesn’t even have access to. This ability could of course be repurposed to do much more evil things.
Whilst on paper at least these exploits were very bad news and they do affect billions of devices, an attacker would of course need to be in the vicinity of a network to be able to screw with it. So bad guys taking advantage of these vulnerabilities on a large scale just isn’t realistic.
Solar Winds Hack
In reality the Solar Winds hack took place between 2019 and 2020. However we first learned of the hack on December 13th of 2020 - but many details of the hack only really started being published months later, simply because the effects were so widespread and deep - as such I'm including it in this list!
It’s suspected that Russian state backed hackers belonging to the groups “Berserk bear” and “Cozy bear” were behind the operation which targeted the “Orion platform”, developed by solar winds. “Orion” is an IT management tool used to monitor and control fleets of computers.
Somehow the miscreants managed to gain a foothold in the build system of solarwinds. The build system handles compiling code into the final executables, if a bad actor could gain access to it, then they could modify the software before it was sent to solar winds’ thousands of customers. We don’t know exactly how solarwinds was initially compromised, though in an SEC filing solar winds seems to blame a compromised “Office 365” account, saying this “may have provided access” to “productivity tools”.
The hackers injected malicious code which gave them access to each system solar winds orion was deployed on - which included a lot of high value targets. There’s the “US department of the treasury”, “U.S. National Nuclear Security Administration”, “Department of homeland security” and so on - the victims are a diverse bunch, it affected both public and private sector organisations.
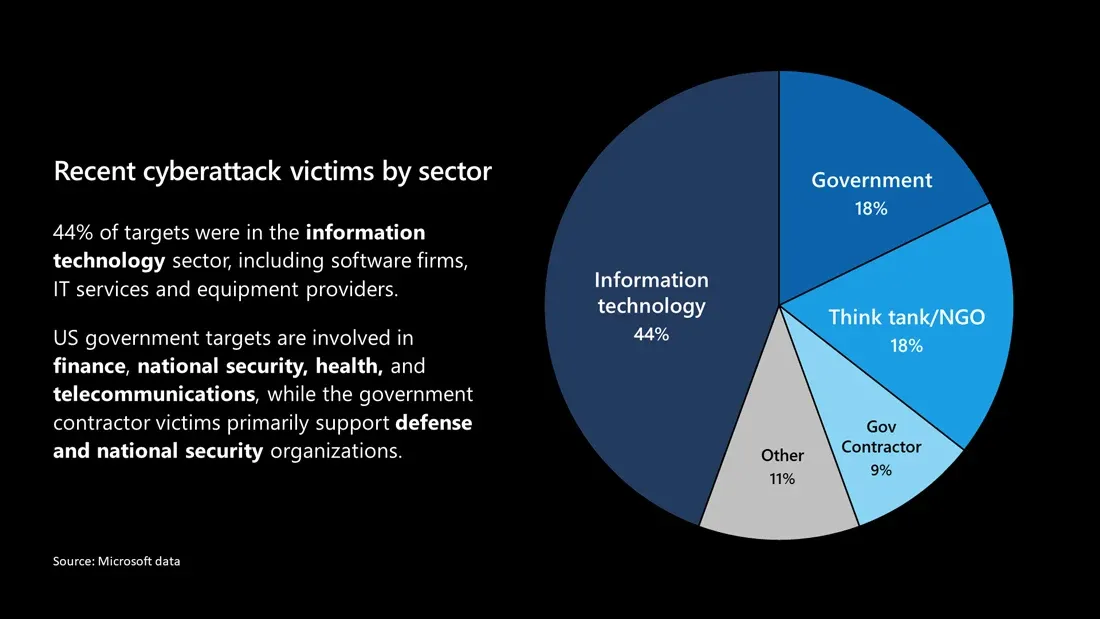
It was such a monumental hack that some even questioned whether it should be designated an “act of war” - though thankfully this idea was quickly rejected.