You can also watch this video on LBRY
- Tojan of raided cybercriminal gang is back and improved
- The malware uses a simple cipher to avoid detection
- Analysis by Checkpoint and ESET demystifies the malware
Mekotio
Mekotio is a banking trojan thought to be the work of Brazilian cybercriminals. 16 members of it's Spanish counterparts were arrested in July 2021. Not to be deterred the gang swiftly reengineered their trojan, making it more stealthy.
Desarticulada una red dedicada a cometer estafas a través de Internet.
— Guardia Civil 🇪🇸 (@guardiacivil) July 10, 2021
Se ha detenido a 16 personas y se han conseguido bloquear tentativas de transferencias por un importe de 3.500.000 euros, tras analizar más de 1.800 correos electrónicos.
Más info: https://t.co/0ggQlE0UxB pic.twitter.com/EOAVRuyrKq
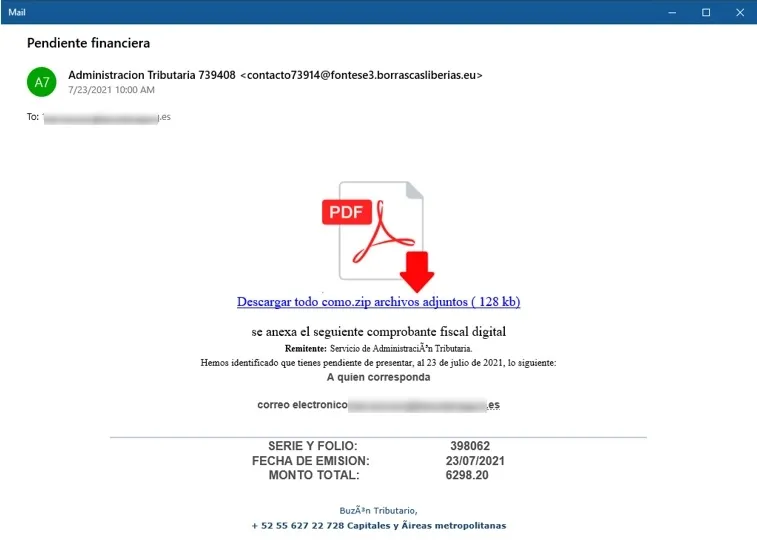
Mekotio spreads by use of phishing emails, purporting that the victim owes a sum of money - prompting them to download a pdf file to view the invoice. The downloaded zip file contains a malicious batch script which once executed loads Mekotio onto the victim PC.
Cipher obfuscation
Mekotio uses a very primitive cipher in order to obfuscate its code, outsmarting antivirus products.
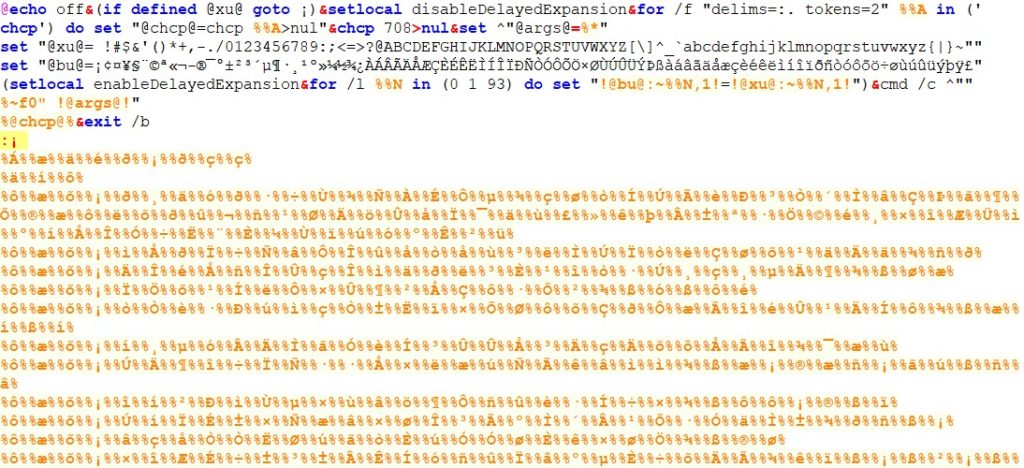
Checkpoint explains: "This simple obfuscation technique allows it to go undetected by most of the AntiVirus products ... Each batch file contains these two lines"
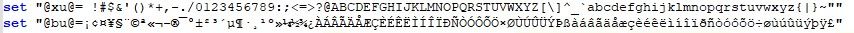
At runtime characters from the bottom set are mapped onto the corresponding character in the top set, de-obfuscating the code.